Security vulnerability in the iPhone's USB-C port and a trap with iMessage phishing scams
A security vulnerability has been discovered in the built-in USB-C controller of the iPhone 15 and 16. However, exploiting this vulnerability would be so complex that both Apple and the security researcher who discovered it conclude that it is not a real threat in the real world.
However, a security concern that poses a danger to iPhone users is a strategy used by scammers to bypass one of Apple's built-in protections...
Security Vulnerability in the USB-C Port of the iPhone
The security researcher Thomas Roth discovered a vulnerability in the USB-C cable controller chip introduced for the first time in Apple's supply chain in 2023. In principle, it could be used to compromise an iPhone, as reported by Cyber Security News.
Security researchers have successfully hacked the proprietary ACE3 USB-C controller owned by Apple. This chip, introduced with the iPhone 15 and iPhone 15 Pro, represents a significant advancement in USB-C technology, managing power delivery and acting as a sophisticated microcontroller with access to critical internal systems [...]
The Roth group succeeded in executing code on the ACE3 processor. By carefully measuring electromagnetic signals during the processor's startup, they identified the exact moment when firmware validation occurred.
The use of an electromagnetic fault injection at this critical stage allows them to bypass validation checks and start a modified microprogram fix in the chip's processor.
In theory, this could give an attacker complete control over an iPhone.
However, it would require physical access to the device and is extremely difficult to implement. Macworld reports that Apple concluded it was not a real threat after examining the method used, and Roth agreed with this.
Tactic Used by Scammers via iMessage Can Bypass Protocols
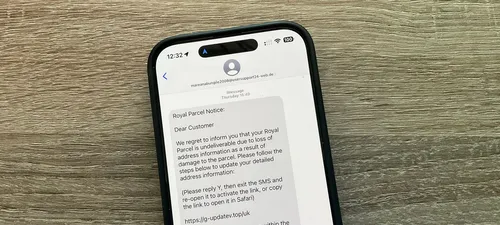
SMS and iMessages are frequently used by scammers to send links designed for phishing attacks and to try to install malware on iPhones.
To protect against this, if you receive an iMessage from someone not in your contacts and with whom you have never exchanged messages, your iPhone automatically disables all the message links. They appear as plain text and cannot be touched.
However, scammers have found a way to bypass this. If they can convince you to respond to the message, even with a STOP command intended to instruct a legitimate sender not to send any more messages, then this protection is disabled.
BleepingComputer says that addressing them, even with a single character response, means that your iPhone considers them legitimate and unlocks their links.
Apple informed BleepingComputer that if a user responds to this message or adds the sender to their contact list, the links will be activated.
In recent months, BleepingComputer has observed an increase in SMS phishing activity trying to get users to respond to a text message so that the links can be reactivated.
The site showed examples of false texts claiming to come from the USPS and a highway company, each asking the person received to reply with Yes. This would activate the links.
It's quite common for me to find the example above simply by looking in my spam folder.
How to Protect Yourself
Never click on a link received via email or in other messages unless you are explicitly invited to do so. The best practice is always to use your own bookmarks or manually type URLs, and only if you have a good reason to believe the message is authentic. When in doubt, call or send a message to the company using known contact details to verify.
- Here's how to protect against password reset attacks on an iPhone.
- Apple shares how to protect your Apple ID, avoid scams and other frauds
Catégories
Derniers articles
- <p>Examen du clavier mécanique Satechi Keyboard SM3 : silencieux et parfait pour la productivité</p>
- This old phone became a fire hazard right before my eyes.
- 10 façons dont l’invitation d’Apple diffère du Calendrier Apple
- <p>Apple au travail : 2025 sera-t-il l’année où Apple lancera un concurrent de Google Workspace ?</p>
- Apple improbable d'organiser un événement spécial pour annoncer l'iPhone SE 4.
- Indices et solutions du jeu « Connections » du NYT pour le 8 février (#608)" Let me know if you'd like me to translate this into another language! 😊
- Support for Ubuntu 20.04 LTS is ending.
- Avez-vous une liste de lecture ? Laissez l'IA vous lire.
- Voici mon lecteur Blu-ray du Graal.
- <p>De nouveaux produits Apple seront lancés la semaine prochaine : voici ce qui arrive.</p>
Derniers tags
- rétroéclairage
- compatible
- silencieux
- recyclage
- danger
- gonflées
- Batteries lithium-ion
- Workspace
- Communiqué
- Annonce