iPhoneのUSB-Cポートのセキュリティ脆弱性、およびiMessage詐欺に関する注意点
The security vulnerability found in the USB-C port controller of iPhones 15 and 16 is very complex to exploit, as Apple and its discoverer, a security researcher, concluded that it does not present a real-world threat.
However, there are security concerns for iPhone users that could be exploited by fraudsters. They use techniques that bypass Apple's built-in protective features.
Security Vulnerability of USB-C Port on iPhones
Security researcher Thomas Los discovered a vulnerability in the USB-C controller chip introduced by Apple's supply chain in 2023. Theoretically, this could be used to attack an iPhone.
The security researchers successfully hacked Apple's proprietary ACE3 USB-C controller. This chip is used in iPhone 15 and iPhone 15 Pro and represents a significant advancement in USB-C technology. It processes power supply and acts as a highly advanced microcontroller with access to important internal systems.
Los' team achieved code execution on the ACE3 chip by precisely measuring electromagnetic wave signals during the boot process, identifying the moment when firmware verification occurs.
At this crucial timing, they used electromagnetic fault injection to bypass the verification checks and launch a modified firmware patch on the chip's CPU.
Theoretically, this could give attackers complete control over an iPhone.
However, it requires physical access to the device, which is very difficult to achieve. Macworld confirmed that Apple verified the method used by Los' team and concluded that it was not a real threat. Roth also agreed with this conclusion.
iMessage Scam Techniques Can Bypass Security Features
SMS and iMessages are often used by scammers to send links for malware installation on iPhones.
To address this issue, if you receive an iMessage from someone not in your contacts and have no experience exchanging messages with them, the iPhone automatically invalidates any links within the message. The link is displayed as normal text and cannot be opened.
However, scammers discovered how to bypass this protection. By responding to a message and giving instructions to not contact the legitimate sender again, they can disable this protection.
According to BleepingComputer, even sending just one reply to a message will make the iPhone judge the user as legitimate or suspicious and unblock the link.
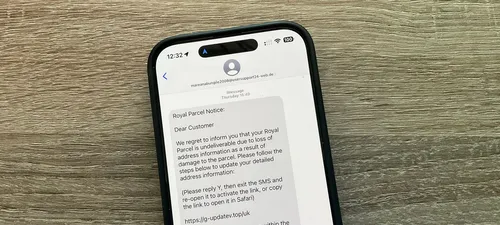
"If a user replies to the message or adds the sender to their contact list, the link becomes active."
A few months ago, BleepingComputer observed an increase in phishing attacks that诱导 users to respond to texts to re-enable links.
The site provided examples of suspected fake text messages from USPS and road companies. Each message asked the recipient to reply with 'Y' to activate the link.
"This is common, so you can find these examples by looking at the deleted message folders."
Self-Protection Methods
Do not click or tap on links received via email or other messages. The best practice is always to use your bookmarks or manually enter URLs. For the latter, only do it if you are confident that the message is true. If unsure, contact the company using a known contact and confirm by phone or sending a message.
- Methods to protect against iPhone password reset attacks
- "How Apple Protects Your Apple ID from Phishing and Other Scams"
カテゴリー
最新記事
- 静かなキーストロークと高い生産性の向上を実現する、STEALTH KEYBOARD SM3 メカニカルキーボードのレビュー。
- その古い電話が目の前で火事の原因になった。
- アップル招待とアップルカレンダーの違い:10個のポイント
- アップル @ ワーク:2025年にアップルがGoogle Workspaceに対抗する製品をリリースするのか?
- Apple は iPhone SE 4 を発表する特別なイベントを開催する可能性が低い。
- 今日の NYT Connections ヒントと解答 (2 月 8 日 #608)
- Ubuntu 20.04 LTS のサポートが終了します。
- 読み込みが間に合わない? AI に読んでもらいたいですか?
- これは私が愛用する聖杯 ブルーレイプレーヤーです。
- 来週、新しい Apple 製品の発表が予定されています。詳細は下記の通りです。