<p><strong>安全提示:黑客如何利用蓝牙控制你的 Mac</strong></p>

Moxi, the only platform dedicated to Apple's unified ecosystem. We are committed to making Apple devices readily available and enterprise-secure. Our unique integrated management and security approach combines cutting-edge Apple-specific security solutions to achieve fully automated hardening and compliance, next-generation EDR, AI-powered zero trust, and exclusive privilege management, all powered by the most robust and modern Apple MDM on the market. The result is a fully automated Apple unified platform trusted by over 45,000 organizations, helping them easily deploy millions of Apple devices at an affordable cost. Request an extended trial today to experience why Moxi is everything you need to partner with Apple.
In Bluetooth impersonation attacks (or BIAS), hackers can exploit vulnerabilities in the Bluetooth protocol to masquerade as trusted devices. "Bose QuietComfort Headphones" appearing on your Bluetooth menu could be a Trojan horse, waiting for you to connect before unleashing havoc.
This week's security briefing will demonstrate how hackers can use Flipper Zero to send hidden keystrokes to a Mac by connecting to a fabricated Bluetooth device. Since there are numerous guides available, this won't be a comprehensive tutorial. I simply want to highlight the ease of accomplishing this and raise your awareness.
Out of the box, Flipper Zero is a relatively harmless penetration testing tool. However, due to its open-source nature, it can be modified with third-party firmware (in this case, Xtreme) to provide a range of applications that leverage the device's feature-rich hardware resources – similar to the same Xtreme used in 2023 to crash iPhones via fabricated BLE pairing sequences.
One such application is a wireless rubber ducky keyboard called "Bad USB," which also supports Bluetooth Low Energy (BLE). Primarily used for automating tasks or testing device security by simulating keyboard inputs faster than humans and executing scripts with ease. Combined with BLE's 100-meter transmission range, it makes this an attractive tool for hackers.
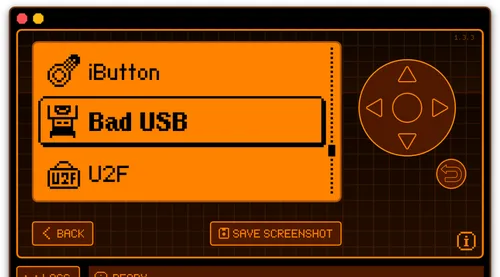
In just four steps and 20 minutes, I successfully executed a Rickroll script on a MacBook Air.
- On Flipper Zero, activate the Bad USB module using the Xtreme firmware.
- Upload your chosen payload to Flipper. I created my own .txt script to open YouTube.
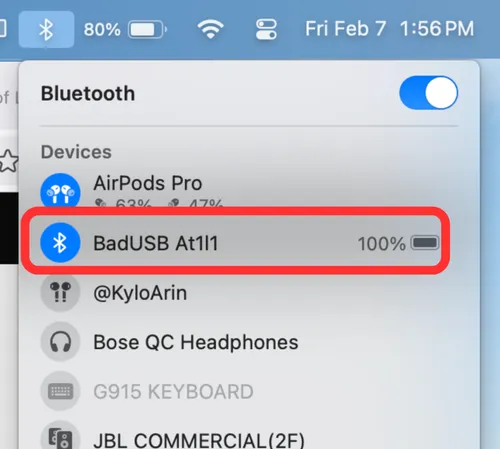
- Choose a clever Bluetooth device name and connect to it. Since I live in a densely populated urban area, I kept the default name (BadUSB At1l1).
- Once pairing is displayed, execute the payload.


This isn't just a problem for Mac computers. These attacks can also target iPhones, iPads, and Windows devices. Of course, attackers would inflict consequences far worse than a Rick Astley song.
Victim Perspective
Mitigation Measures
The good news is that this only works when the device is unlocked. The bad news is that most people aren't very cautious about connecting Bluetooth devices. It's crucial to confirm you're connecting to the intended device (thankfully, AirPods have the H2 chip), as malicious actors can use multiple devices with names very similar to legitimate ones. They can also operate using spoofed MAC addresses, making identification harder.
Prevent becoming a victim by disabling unused Bluetooth functionality, removing unknown devices from your Bluetooth settings list, and utilizing six-digit pairing codes.
While these attacks are relatively uncommon, that doesn't mean they never happen. I believe their frequency is enough to raise some concern, although many victims remain unaware because these attacks often occur secretly in the background. Hackers love persistence. Why would they destroy one Mac in a single attack when they can keep coming back for more?
Follow Arin: Twitter/X, LinkedIn, Threads
分类
最新文章
- <p><strong>Satechi SM3 机械键盘测评:安静高效的生产力利器</strong></p>
- This old mobile phone has become a fire hazard right before my eyes.
- <p>苹果日历的邀请函:与苹果待办事项有10种不同之处</p>
- <p><strong>苹果的工作:</strong> 2025 年苹果会发布一个与谷歌 Workspace 竞争的产品吗?</p>
- <p>苹果不太可能会举办特别活动来宣布 iPhone SE 4。</p>
- Today's New York Times Crossword Puzzle Clues and Answers (#608)
- Ubuntu 20.04 LTS 的支持即将到期。
- <p>读书清单太长了吗?让 AI 为您朗读。</p>
- This is my holy grail Blu-ray player.
- <p>Apple will release new products next week. Here's what's coming.</p>